[ad_1]
On Thursday night, KrebsOnSecurity was the topic of a somewhat huge (and mercifully transient) distributed denial-of-service (DDoS) assault. The assault got here from “Meris,” the identical new botnet behind record-shattering assaults in opposition to Russian search large Yandex this week and web infrastructure agency Cloudflare earlier this summer time.

Cloudflare not too long ago wrote about its assault, which clocked in at 17.2 million bogus requests-per-second. To place that in perspective, Cloudflare serves over 25 million HTTP requests per second on common.
In its Aug. 19 writeup, Cloudflare uncared for to assign a reputation to the botnet behind the assault. However on Thursday DDoS safety agency Qrator Labs recognized the offender — “Meris” — a brand new monster that first emerged on the finish of June 2021.
Qrator says Meris has launched even larger assaults since: A titanic and ongoing DDoS that hit Russian Web search large Yandex final week is estimated to have been launched by roughly 250,000 malware-infected gadgets globally, sending 21.8 million bogus requests-per-second.
Whereas final evening’s Meris assault on this web site was far smaller than the current Cloudflare DDoS, it was far bigger than the Mirai DDoS assault in 2016 that held KrebsOnSecurity offline for almost 4 days. The visitors deluge from Thursday’s assault on this web site was greater than 4 occasions what Mirai threw at this web site 5 years in the past. This newest assault concerned greater than two million requests-per-second. By comparability, the 2016 Mirai DDoS generated roughly 450,000 requests-per-second.
In keeping with Qrator, which is working with Yandex on combating the assault, Meris seems to be made up of Web routers produced by MikroTik. Qrator says the US is residence to essentially the most variety of MikroTik routers which might be probably susceptible to compromise by Meris — with greater than 42 % of the world’s MikroTik methods linked to the Web (adopted by China — 18.9 %– and an extended tail of one- and two-percent international locations).
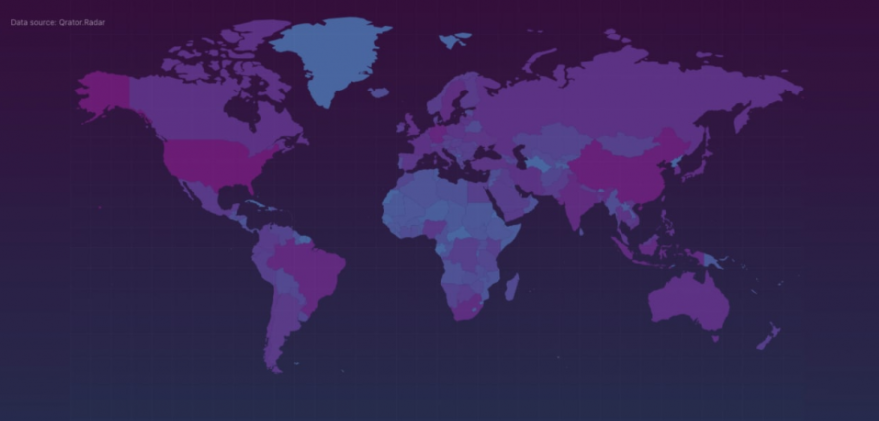
The darker areas point out bigger concentrations of probably susceptible MikroTik routers. Qrator says there are about 328,000 MikroTik gadgets presently responding to requests from the Web. Picture: Qrator.
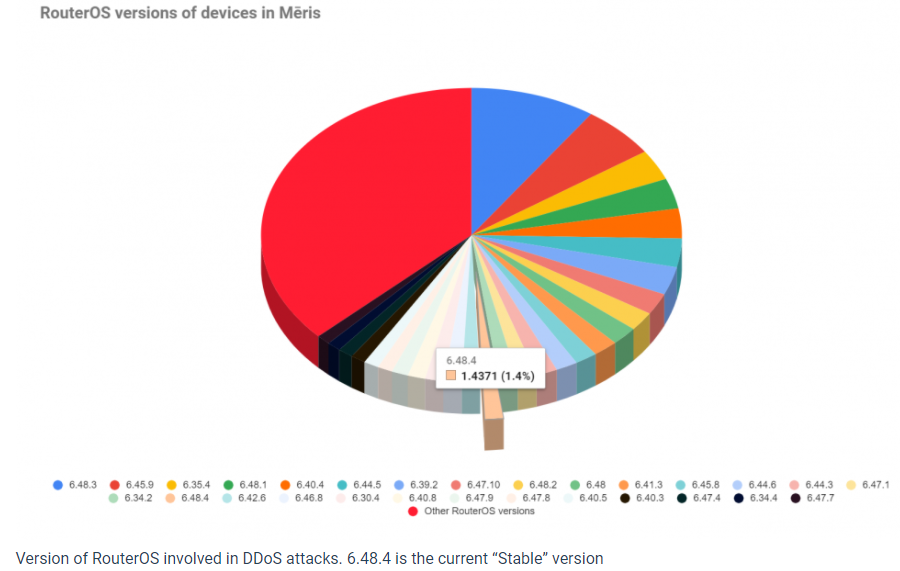
It’s not instantly clear which safety vulnerabilities led to those estimated 250,000 MikroTik routers getting hacked by Meris.
“The spectrum of RouterOS variations we see throughout this botnet varies from years outdated to current,” the corporate wrote. “The biggest share belongs to the model of firmware earlier to the present steady one.”
It’s becoming that Meris would rear its head on the five-year anniversary of the emergence of Mirai, an Web of Issues (IoT) botnet pressure that was engineered to out-compete all different IoT botnet strains on the time. Mirai was extraordinarily profitable at crowding out this competitors, and rapidly grew to contaminate tens of hundreds of IoT gadgets made by dozens of producers.
After which its co-authors determined to leak the Mirai supply code, which led to the proliferation of dozens of Mirai variants, lots of which proceed to function at this time.
The most important contributor to the IoT botnet drawback — a plethora of corporations white-labeling IoT gadgets that have been by no means designed with safety in thoughts and are sometimes shipped to the shopper in default-insecure states — hasn’t modified a lot, primarily as a result of these gadgets are usually far cheaper than safer alternate options.
The excellent news is that over the previous 5 years, massive Web infrastructure corporations like Akamai, Cloudflare and Google (which protects this web site with its Mission Defend initiative) have closely invested in ramping up their capability to face up to these outsized assaults [full disclosure: Akamai is an advertiser on this site].
Extra importantly, the Web group at massive has gotten higher at placing their heads collectively to combat DDoS assaults, by disrupting the infrastructure abused by these huge IoT botnets, stated Richard Clayton, director of Cambridge College’s Cybercrime Centre.
“It will be honest to say we’re presently involved about a few botnets that are bigger than we have now seen for a while,” Clayton stated. “However equally, you by no means know they might peter out. There are lots of people who spend their time making an attempt to ensure this stuff are arduous to maintain steady. So there are individuals on the market defending us all.”
[ad_2]