[ad_1]
A focused phishing marketing campaign aimed on the aviation trade for 2 years could also be spearheaded by a risk actor working out of Nigeria, highlighting how attackers can perform small-scale cyber offensives for prolonged durations of time whereas staying below the radar.
Cisco Talos dubbed the malware assaults “Operation Layover,” constructing on earlier analysis from the Microsoft Safety Intelligence group in Might 2021 that delved right into a “dynamic marketing campaign concentrating on the aerospace and journey sectors with spear-phishing emails that distribute an actively developed loader, which then delivers RevengeRAT or AsyncRAT.”
“The actor […] would not appear to be technically refined, utilizing off-the-shelf malware for the reason that starting of its actions with out growing its personal malware,” researchers Tiago Pereira and Vitor Ventura mentioned. “The actor additionally buys the crypters that enable the utilization of such malware with out being detected, all through the years it has used a number of completely different cryptors, largely purchased on on-line boards.”
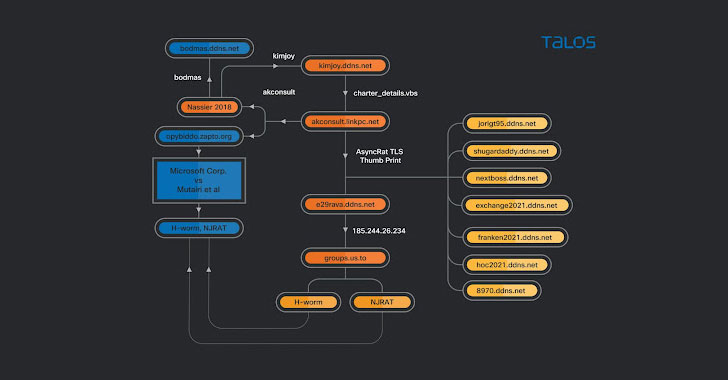
The risk actor is believed to have been lively no less than since 2013. The assaults contain emails containing particular lure paperwork centered across the aviation or cargo trade that purport to be PDF information however hyperlink to a VBScript file hosted on Google Drive, which finally results in the supply of distant entry trojans (RATs) like AsyncRAT and njRAT, leaving organizations susceptible to an array of safety dangers. Cisco Talos mentioned it discovered 31 completely different aviation-themed lures courting all the best way again to August 2018.
Additional evaluation of the exercise related to completely different domains used within the assaults present that the actor weaved a number of RATs into their campaigns, with the infrastructure used as command-and-control (C2) servers for Cybergate RAT, AsyncRAT, and a batch file that is used as a part of a malware chain to obtain and execute different malware.
“Many actors can have restricted technical information however nonetheless have the ability to function RATs or information-stealers, posing a big danger to massive firms given the best circumstances,” the researchers mentioned. “On this case, […] what appeared like a easy marketing campaign is, in truth, a steady operation that has been lively for 3 years, concentrating on a complete trade with off-the-shelf malware disguised with completely different crypters.”
[ad_2]