[ad_1]
Because the Nationwide Safety Company publicly launched the software program reverse engineering (SRE) instrument suite, we now have been working to combine Ghidra into our Pharos malware evaluation instrument. Ghidra offers many helpful reverse engineering providers together with disassembly, operate partitioning, decompilation, and numerous different sorts of program analyses. As this submit particulars, we now have been creating a brand new suite of instruments, generally known as Kaiju, for malware evaluation and reverse engineering to reap the benefits of Ghidra’s capabilities and interface. Ghidra offers a compelling surroundings for reverse engineering instruments which might be comparatively straightforward to make use of throughout malware evaluation. The instruments included with Kaiju give malware analysts many benefits as they’re confronted with more and more various and complicated malware threats.
Ghidra helps working a lot of user-developed plug-ins on the identical time. We wished to leverage this function to combine a number of instruments we developed for extra correct static evaluation of executable code. Having a standard graphical consumer interface (GUI) makes it simpler to maintain monitor of the additional options being introduced. Tighter integration of the instruments additionally ensures lower-level analyzers get executed first, so gaps within the evaluation are stuffed in and incorrect info are corrected previous to being utilized by higher-layer plug-ins. A typical framework additionally makes managing all of the plug-ins simpler to put in and run.
Kaiju contains Ghidra/Java implementations of many options of the CERT Pharos Binary Evaluation Framework, notably the operate hashing and malware evaluation instruments. On this submit, we focus on Kaiju and the instruments included that use Ghidra’s analytics. We additionally describe the Pharos instruments that we now have ported to work with Ghidra as a part of Kaiju. Lastly, other than being a framework for putting in and working The CERT Division’s Ghidra plug-ins, Kaiju offers a number of built-in utilities and providers that may help reverse engineering and malware evaluation.
New Evaluation Instruments Included in Kaiju
All of the instruments in Kaiju use Ghidra for analytical data and providers, resembling disassembly and performance partitioning. Furthermore, just a few instruments mentioned under reap the benefits of Ghidra’s superior capabilities.
GhiHorn
GhiHorn is a instrument that makes use of the Z3 Theorem Prover to purpose about reachable paths by a binary. As we famous in a earlier weblog entry, path discovering might be an insightful strategy to malware evaluation actions. Understanding the situations obligatory to succeed in a particular level in a program might be invaluable for bypassing anti-analysis methods, recovering significant information, and figuring out fascinating behaviors.
In our Pharos implementation of path discovering, we used symbolic values and management movement graphs to generate constraints that assist consider whether or not a path is possible or not. With Ghidra, we switched to utilizing information generated throughout decompilation. This strategy has an a variety of benefits over our earlier strategy. Our older path discovering instruments have been restricted in lots of facets of path evaluation, resembling loop evaluation imprecision and sensitivity to nuances ensuing from compilation and optimization. Ghidra’s decompilation and intermediate illustration of program semantics (generally known as P-code), paired with a specialised encoding generally known as Constrained Horn Clauses geared in direction of reachability issues, provide a compelling new avenue for path discovering.
Lastly, a standard problem with program evaluation instruments issues the issue in deciphering outcomes. Happily, Ghidra’s GUI offers many options with which to show evaluation data, resembling interactive graphs. GhiHorn makes use of these options to indicate outcomes to analysts in an actionable, helpful manner. GhiHorn contains two utilities to help reverse engineering: PathAnalyzer, which determines the situations to succeed in a given level of a program, and ApiAnalyzer, which assesses if a habits is current in an executable file based mostly on interactions with the underlying system.
We’re planning a devoted weblog submit sooner or later on how GhiHorn works, so keep tuned!
Perform Set Extractor and Visualizer
This utility permits an analyst to check capabilities throughout packages in the identical Ghidra undertaking utilizing operate hashes. Determine 1 exhibits the Perform Set Intersection Visualizer in motion. Every row of the desk identifies the hashes that we present in every program in a Ghidra undertaking.
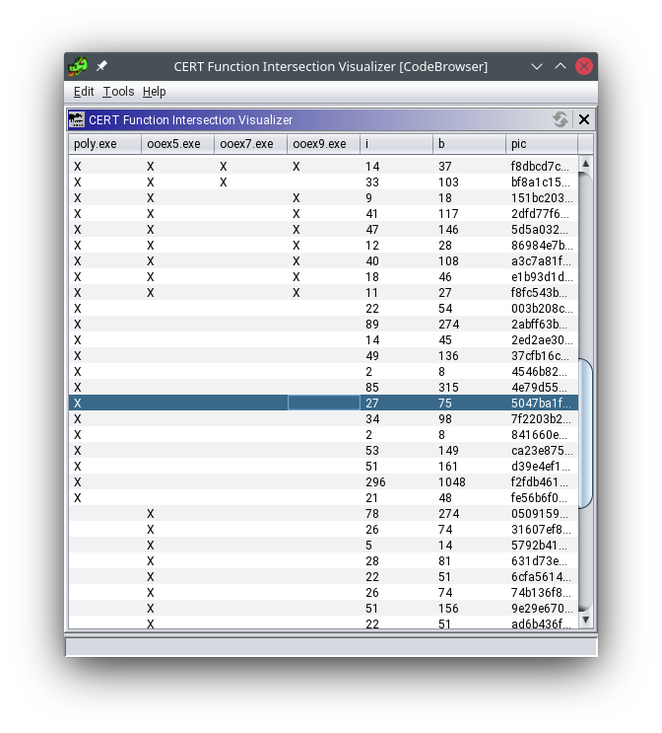
Determine 1: Perform Set Intersection Visualizer
Perform Hash Viewer
This instrument is a graphical utility used to view operate hashing information for a program in Ghidra. Determine 2 exhibits the Perform Hash Viewer evaluating completely different hashes for a particular operate.
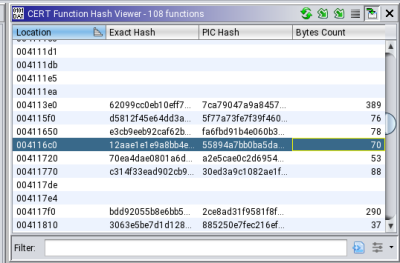
Determine 2: Perform Hash Viewer
Fnxrefs
The Fnxrefs instrument generates a cross-references desk for Ghidra. The desk shows addresses in a given program which might be referenced by different information and/or code in this system. Determine 3 exhibits the Fnxrefs consumer interface. The desk is sortable to allow analysts to simply discover probably the most referenced capabilities and information in a program.
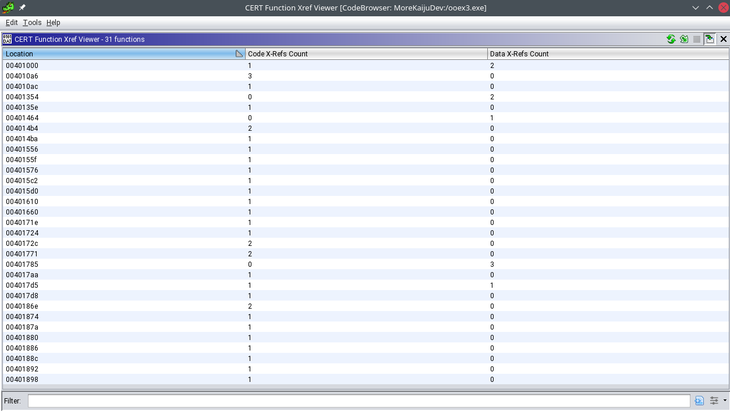
Determine 3: Fnxrefs Desk
CERT Pharos Instruments in Ghidra
Other than the brand new instruments in Kaiju, we now have ported a lot of present Pharos instruments to work with Ghidra. These instruments have been initially developed as a part of the Pharos Binary Evaluation Framework based mostly on the ROSE Compiler framework. Basically, these instruments behave the identical as they did in Pharos, however now use Ghidra because the evaluation engine.
CERT Disassembly Enhancements
Kaiju features a utility to replace Ghidra’s disassembly, based mostly on our experiences with reverse engineering malware. This utility mechanically processes undefined addresses, gaps within the disassembly, and different nuances that we frequently see in Ghidra tasks. These enhancements are carried out as a Ghidra analyzer, which might be run on demand or mechanically throughout preliminary evaluation of the binary. The enhancements embody higher evaluation of gaps within the file, corrected alignment points, and the power to uncover new code or code that was not discovered throughout partitioning. These adjustments are geared towards dealing with malware executables which will embody obfuscations or code preparations designed to thwart evaluation.
Fn2YARA
Fn2YARA (Perform-to-YARA) is a instrument that generates YARA signatures for matching capabilities in an executable program. Applications that share vital numbers of capabilities are more likely to have habits in frequent, and YARA signatures make it straightforward to seek for comparable capabilities.
Fn2Hash
Fn2Hash (Perform-to-Hash) is a instrument for producing quite a lot of hashes and different descriptive properties for capabilities in an executable program. Like Fn2Yara, it may well help binary similarity evaluation or present options for machine studying algorithms.
OOAnalyzer JSON Importer
OOAnalyzer (Object-Oriented-Analyzer) is one among our most superior and best-maintained plug-ins. The Pharos OOAnalyzer instrument recovers C++-style courses from executables by producing and fixing constraints with Prolog. The OOAnalyzer instrument produces a JSON file with data on recovered C++ courses. The OOAnalyzer JSON importer for Ghidra can import this JSON file into the Ghidra interface. This information is used to reinforce the kind data that’s proven by Ghidra. We at the moment are packaging the OOAnalyzer JSON importer for Ghidra as a part of Kaiju as an alternative of Pharos, as we now have executed previously.
Ghidra Developer Utilities
Other than new instruments, Kaiju additionally features a preliminary set of frequent code utilities that builders can use to create new reverse engineering instruments in Ghidra. Notably, we now have carried out a unified logging framework that simplifies logging code when Ghidra is run in both common graphical interface mode or in command-line headless mode. By appropriately extending or implementing our Java utility courses and interfaces, analysts can also customise Kaiju for the reverse engineering process at hand. We welcome contributions and encourage function requests and bugfixes within the type of GitHub pull requests to the general public repo.
Kaiju Now Out there in Github
Kaiju stays a piece in progress, and we’re frequently updating it and its constituent instruments. The supply code and construct directions for Kaiju can be found on GitHub. We welcome recommendations for enhancements or new utilities that might be most helpful for constructing new instruments to help malware evaluation and reverse engineering. In a future submit we plan to explain the internal working of a few of our extra intensive Ghidra-based instruments.
[ad_2]